Authentication based password would carry on being the key means of user verification for various systems. It is easy to know and maybe fast made to safeguard applications. Though, it is all right only for non-decisive services.
Safety Of Password Dependent Authentication
Various password dependent authentication arrangements are inadequately put up and safeguarded. Into the bargain to attributes like rudely patched tools or indecent SSL pattern, password details itself is regularly accumulated inappropriately. Passwords might be muddled unacceptably, or not as good as, encrypted employing feeble codes and keys. Entry to the password catalog may also not be strongly managed.
The safety of passwords finally is based on the complexity of the user. Managers may attempt to put forth effect through password rules. But an inadequately made, guessable, or escaped password can conciliate an account.
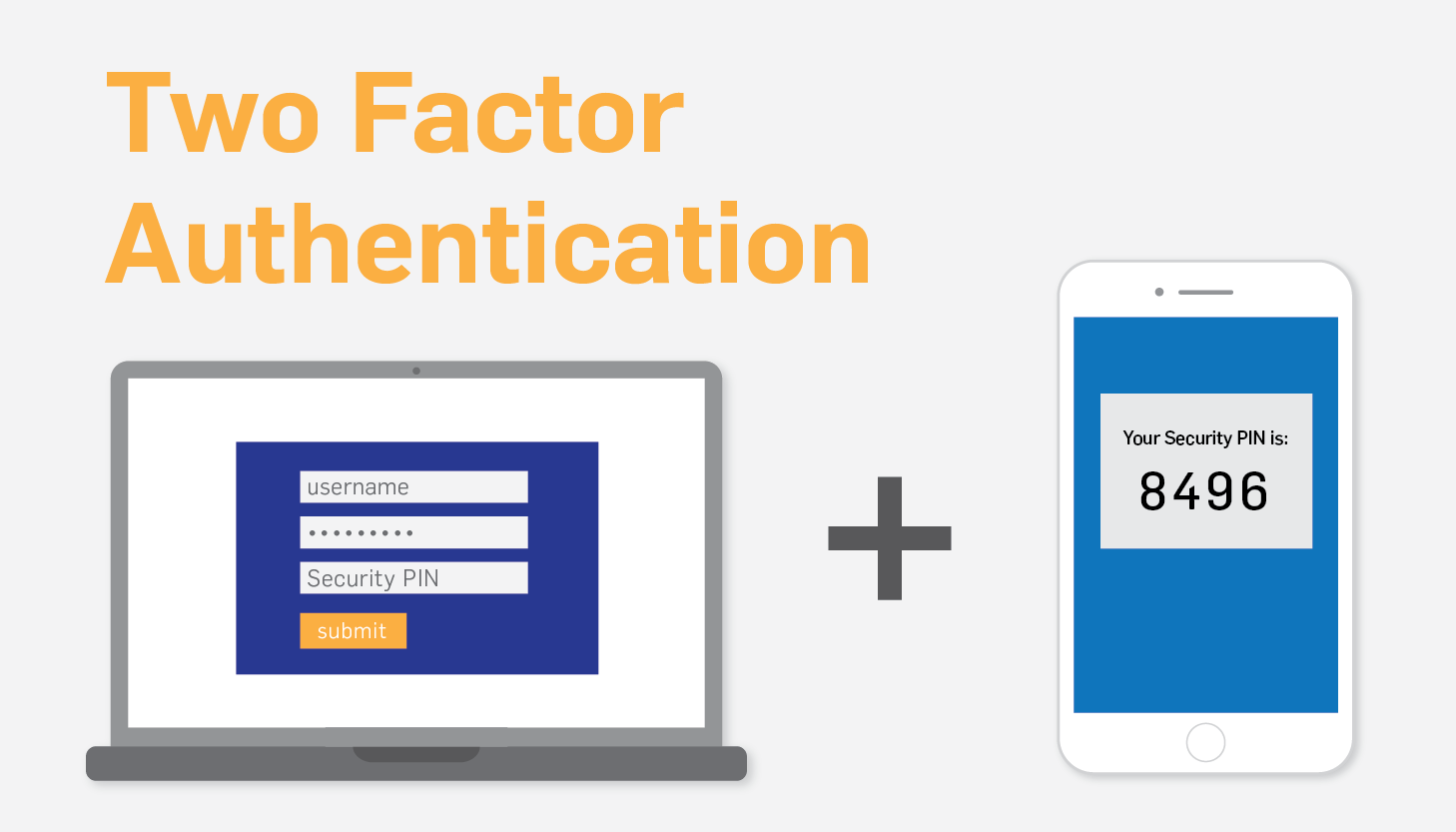
2-factor authentication
2-factor authentication is generally known as 2FA or MFA for multi-factor authentication. It unites checking somewhat you understand in addition to something you possess. For instance, an arrangement might employ password dependent authentication (somewhat you understand) with one-time passcode symbol dependent authentication (somewhat you possess).
One-time Password
One-time password (OTP) is incessantly varying haphazard numbers. They are produced by a tool or through an application on a mobile phone and checked by a server. They may also be delivered through email, push alerts, SMS, or mobile calls.
Working of one-time password
An arbitrary number produced by the application is a task of the present time, and a clandestine, which is allocated by application and server. Both server and application employ a time-dependent one time password dependent algorithm to produce tokens.
When a user registers for a one-time password through an application, they would observe a QR code on the signup display. This QR code is a symbol of a clandestine produced by the server that the application can scrutinize and allocate. The instance or time on application and server are supposed to be in synchronization. The arbitrariness of the clandestine is found out by the server and not managed by the user.
After checking the code, the user finishes the conscription procedure by delivering the server a primary OTP produced by the application. The clandestine is then encoded and allocated on the server in addition to the application and connected to the user’s account.
When a user signs in, the server checks the user quickly for the OTP that the application produces at that instance. The server then decodes the allocated secret fixed to that user, relates to the TOTP dependent algorithm on the clandestine and the present time, produces an OTP, and evaluates it to what the user shows. If the two are similar, it establishes that the user is in control of the application.
Other methods
Also, there are different marketing methods such as transactional email promotion, bulk SMS gateway, SMS software, etc., which also require authentication methods for secured communication. Thus, it is essential for you to ensure user authentication for secured processes.